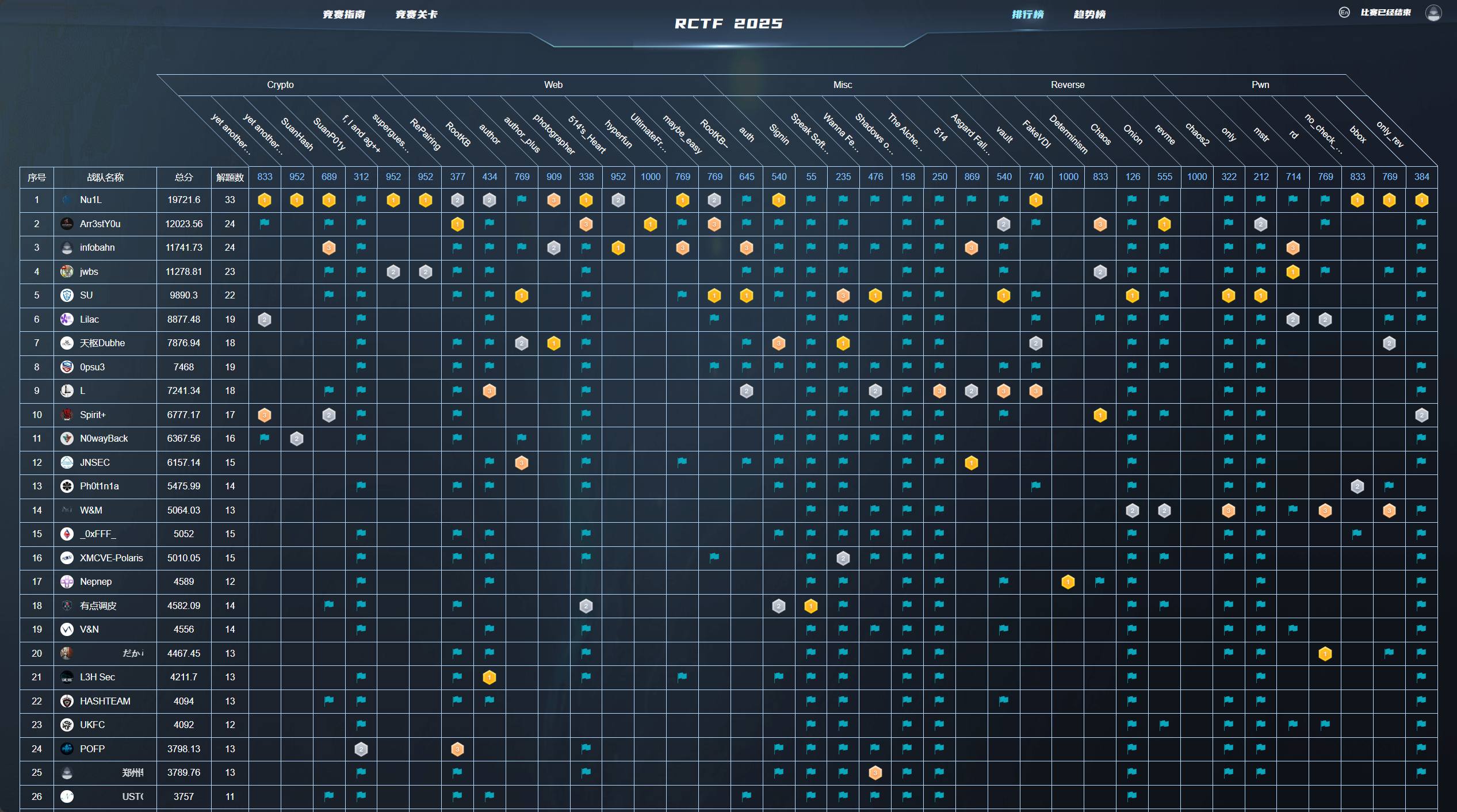
Rank 8
师傅们太强了!!!!冲冲冲!!!
Reverse
Onion
自制调试框架打trace log
1 | |
这边发现在经过一次自定义加密,正确后会进行rc4解密出下一轮的vm字节码,以此类推
用反汇编框架提取每一轮的特征值并返回
1 | |
rc4解密部分
1 | |
解密算法的部分,用位运算代替了加减法,因此在tracelog里显得极其难看。
而其核心就是先进行一段自定义的,每一轮都不同的运算,后面再进入到一个统一的运算中,因为每一轮只需提取前一部分的特征值即可
1 | |
最后写一个统一的解密调度器
1 | |
将最后一轮的vmcode解出来
完整反汇编后最后就可以得到flag
RCTF{VM_ALU_SMC_RC4_SPECK!_593eb6079d2da6c187ed462b033fee34}
chaos
由于比赛平台分数榜计算问题,我们决定将Reverse方向【chaos】重新开放作为签到,并放出对应的Flag:RCTF{AntiDbg_KeyM0d_2025_R3v3rs3}
chaos2
四个反调试点,每个替换一个字节,不用过掉所有的反调试,最多只有2**4 * 2 * 2 中情况,直接遍历一遍,唯一需要关注的点是,密钥被强制填充为了128位,手动补全就行,花指令很好过。
1 | |
Web
Auth
Signature Wrapping attack
后端在校验时是按 type 分支判断要不要校验 invite_code,并且没有对 type 做限制或二次校验
数据库里面type设置的 tinyint类型,所以传字符串,数据库里面会自动转而0存储,然后logout再登录重新刷新session,type就会变为0。 注册时抓包把type值换为string,即可绕过邀请码限制
构造一个新的 assertion(改 NameID 为 admin@rois.team)
SAMLResponsePOST 到 SP 的 /saml/acs,利用 SP 的解析顺序漏洞(取第一个 Assertion 做登录),最终访问 /admin 拿 flag。
1 | |
photographer
登录后上传图片,将图片的 Content-Type 伪造成 -1 ,该值被保存到 photo.type
设置该照片为背景后,用户查询 leftJoin(‘photo’, …) 会让结果集中的 type 列被 photo.type 覆盖
superadmin.php 中比较 Auth::type() < config(‘user_types’)[‘admin’] 即 -1 < 0 为真
直接访问即可获得flag
1 | |
RootKB
创建工具可以执行python代码
覆盖sandbox.so. 打LD_PRELOAD
1 | |
maybe_easy
1 | |
RootKB–
添加工具可以运行python代码
题目提示了有cve,在github里面发现2.3.1修复了sanbox ssrf的漏洞
在sanbox测试一下redis连接
1 | |
发现连接成功,那么说明可以ssrf打redis
审计源码发现celery会信任redis传来的数据并进行pickle loads
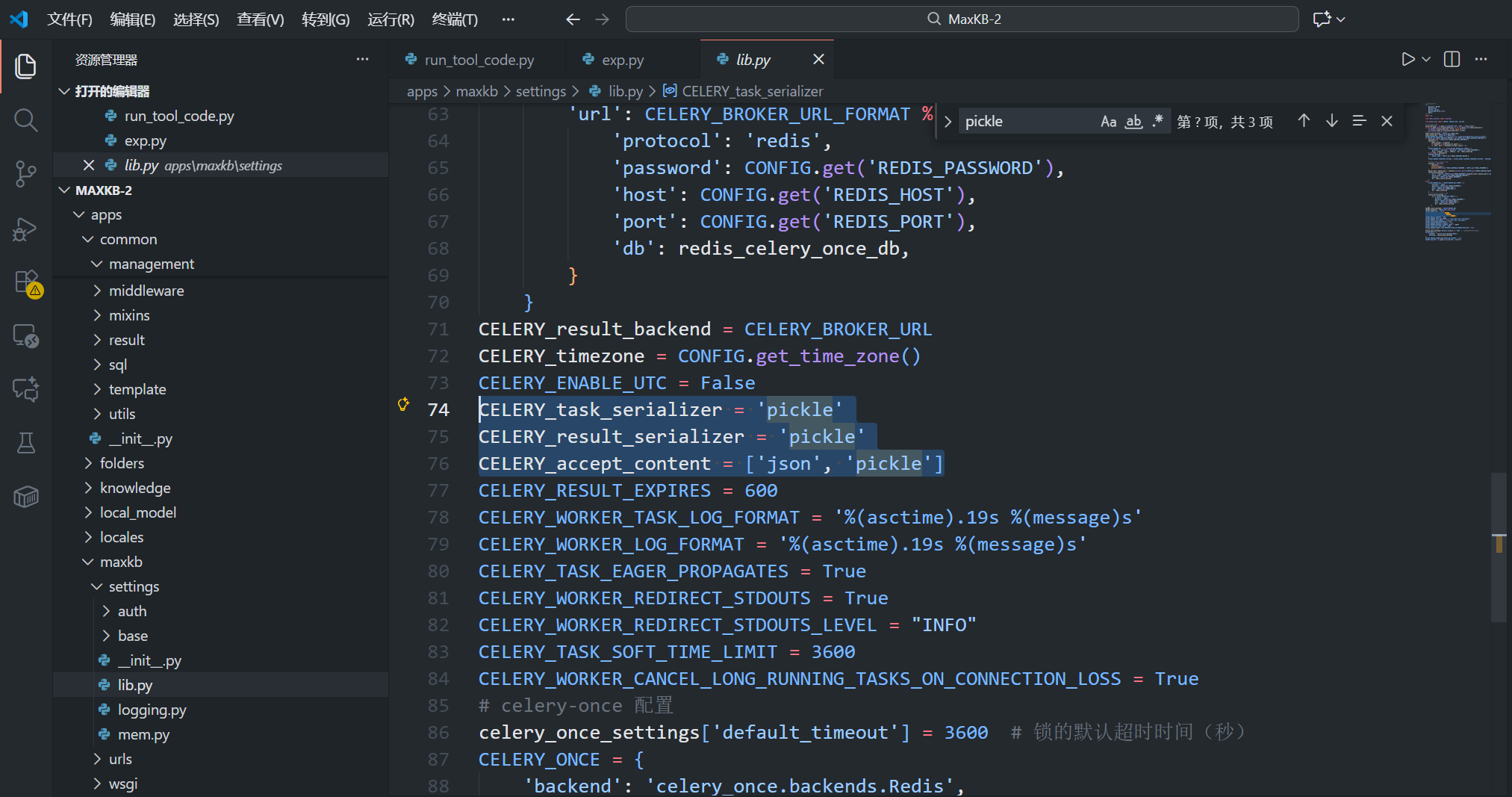
那么思路就是ssrf打redis然后celery pickle反序列化
Exp:
1 | |
然后sanbox读flag
1 | |
Misc
签到
控制台输入以下代码:
1 | |
RCTF{W3lc0m3_T0_RCTF_2025!!!}
Shadows of Asgard
导出http对象,保存随意一个html文件,发现渊恒科技四个字
challenge1:渊恒科技
过滤json
530 19.959810 192.168.77.134 106.52.166.133 HTTP/JSON 1903 POST /assets/cache/5503885e076f4f62.tmp HTTP/1.1 , JSON (application/json)
这个里面发现aeskey aesIV 密文data
写脚本一下:
1 | |
得到结果:
1 | |
challenge2:C:\Users\dell\Desktop\Microsoft VS Code\Code.exe
注意到题目线索“layers of encryption and steganography.”
当时导出http对象时 注意到有一些png 怀疑插入text
依然530 19.959810 192.168.77.134 106.52.166.133 HTTP/JSON 1903 POST /assets/cache/5503885e076f4f62.tmp HTTP/1.1 , JSON (application/json)这个包
找到:MmE2ZGY1ZWJiY2UwODM1OTFmOWJkMjEyNWExNDc1MGNlYTNlYzM5NThmOGNkNjNiZDUxOGJlYzBjODZkZjE3YTAzMjk3MWM1NDVmNjE1ZTY4OGJlNTM4OTgwOTFmYmY2NDczZGIzM2ZlYTZiYjFmOWJiMjBjYjIxNTYzNWViM2I2NzBlZDQxMzNhMGI1OTU2NmNhMGY2YTkyMzBmMDdkZA==
一样的aes key和aes IV
替换一下上面的脚本
得到结果:
1 | |
challenge3:c0c6125e
当将密文替换为:Y2I3MzRjZDFmY2VjY2ZjMzk2OGI5NDUwZTk0NGQzMTc0OGYxZDg0M2FkNTRhNDYwNThiNjFjMjIyZDdjMDdlOGNiNzI4YmNkMDBiMGEzYWM2Mzg3YmM5MjMzMzA1N2U5YTE2ZTZhMjU4NDQ5NDEzMDc1NjY0ZTZjNDg1NzYxYzc5MGQ4ZmExZWQwYzZlZTFiNWIxMjYwYjMzNWU3YmY5NA==的时候,出现结果:
1 | |
看到drive 应该和C盘有关
根据outputChannel 找到相同的
{“agentId”:”vf3d665af4a0ebc4”,”outputChannel”:”o-wup8k5bgwft”,”data”:”ZTdhYmFmMmI5MWJhYzhiNDc0NTA4NTUxNmJjMjI0MDI2MzdkNDc0NmY3MGU5ZmE5ZDk2NjgzZWNkM2Y5Y2NjODZmMzJhNGUxYWZhNDc5ZjJmYmU0NzNlMmU2OTAyNDcwMGE0OTJkMTNkZjMwN2FjNmM3ZWZhYmJiZDU4MjRkNzg2ODYwOTM3YWJkMmIyYTVjMTJiMGZhODJjZDAyZWQ4YmFhNjdiNzJkN2YyN2QwYjM2YTY3MzQxYWVhMDNhNGQ4ZDQ3Y2Y4NWNkOWZiMzZiMTU0ZDk5ZjM2ZmI4ZWE5ZTg5OGEwNmNiMjE5ZGExNzdlZGE1MGYwYmE4NjE0YjNhMzdlMzkwMTEyZGE1NDI2MGIwNGQwMThjM2NmOTc2Y2QyYzdhNWM0ZjM1NzI1OGUzNDMyNWY1N2Y0MDNmYzE0YTA=”,”timestamp”:1763017695848}
写脚本还原一下
1 | |
得到结果:
b’Drive: C:\nCreated: Fri Sep 14 2018 23:09:26 GMT-0700 (Pacific Daylight Time)\nModified: Wed Nov 12 2025 22:52:43 GMT-0800 (Pacific Standard Time)\n—\n\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b’
challenge4:2018-09-14 23:09:26
将M2EyODkyNWFmM2U2MDhlNzJmYjM5ZjA0Zjg2OWYzYTg3YzM1MTNkYzJmZjFmOGJkM2I4ODQwZjE4ZjFhN2E1ZjRhMTM0OWRlNzFmNGU5NjgzZGE4YjE1Y2E5OTE2MWJlODVjYWE0MjNjZGUxMzI4NWM0ZjUyODk0OWE1NWY4YzlmZTc5Mzg2N2U4YTlmM2NlOTczMTQ5NGI0MzVmMmI4MzEwM2ZjMTc5YWY5ODc4MTc3ZjFiMmQwNjcyMzYwNWI4ZWQzZDI0NTZiMDYyODgwM2JiNjAxNDYzZWI5MjFiN2I1NjUwZjY1ZWVmZGEwNzY3MjAwZjVjMmQzNzJlMzQwNGI0M2NiNWFiOTY4MTE4OTUxYjI4YzY5M2I0MmRiNmYyZGZmNzFiN2UxNWMzNWFjZjA4OTQ1ZDQ0MTRmNTY5ZTkwZWM4NDcyZWFlZDE5ZDE3ZjZmODc0NGM4Y2JkOGMyODE0OGUxMDdmMTQzM2NhOWUwYzYzODJlNWVlNzYzODBjY2ZjMGQ0YjhlZDE2MTY3NDJmMDU3MWYzYmM0MmQ1ZjVkMjY4ZTFhM2ZiNDU3OTEzMTJkZTlmNTRjZTFkMjU2OTdiODZmYjExZTM1MWY4MWIwNzliOGRmZjA3ZGQ3ZDhmYzAyZDRkZDY4NjNkNDk5ZDE3ZmRkYTg1NzBkMjMxODNkMzU3N2M5OTcwYjE1YjU5YWZkMzNiYjM2NDVhZDE1Yw==替换进原脚本 得到结果:
1 | |
Base64解码
答案:RCTF{they always say Raven is inauspicious}
综上:RCTF{Wh3n_Th3_R4v3n_S1ngs_4sg4rd_F4lls_S1l3nt}
Asgard Fallen Down
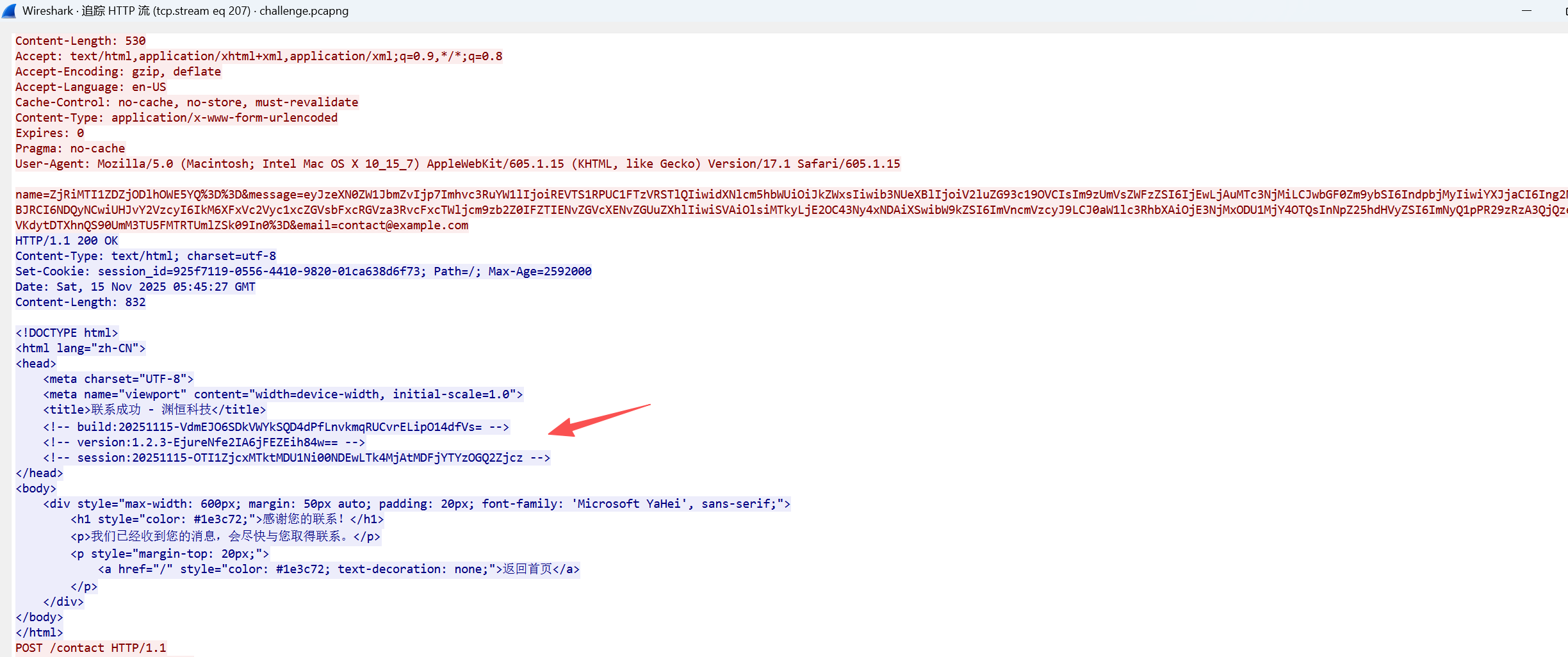
吃了一上午⑩后,发现除了向/connect发送的请求之外,要么404,要么无响应
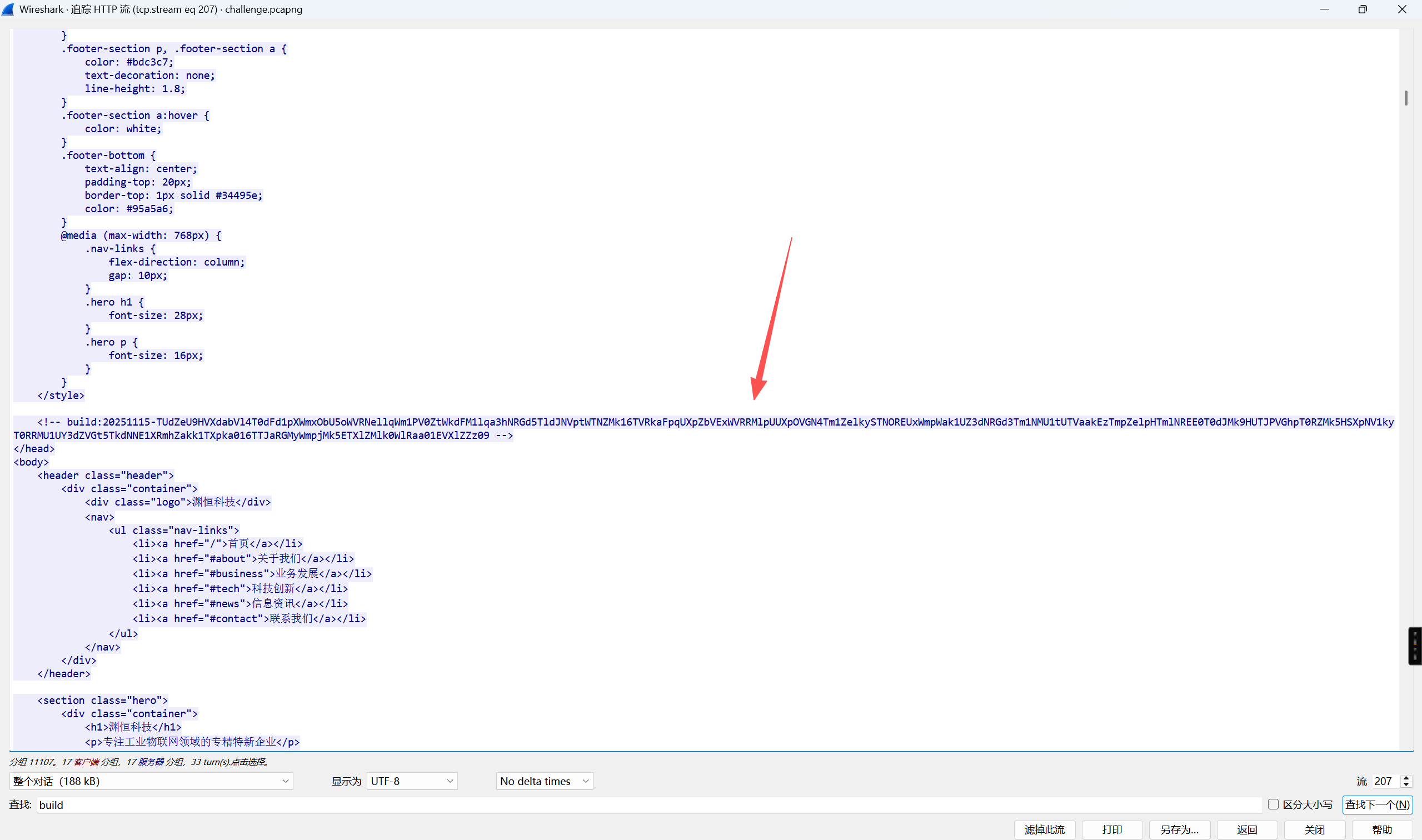
然后在第207个流发现有个不明所以的build和version。然后想到前面就是aes,尝试了一下。后面就是简单的解密了
- 在他的代理建立连接后,洛基执行了第一个什么命令?
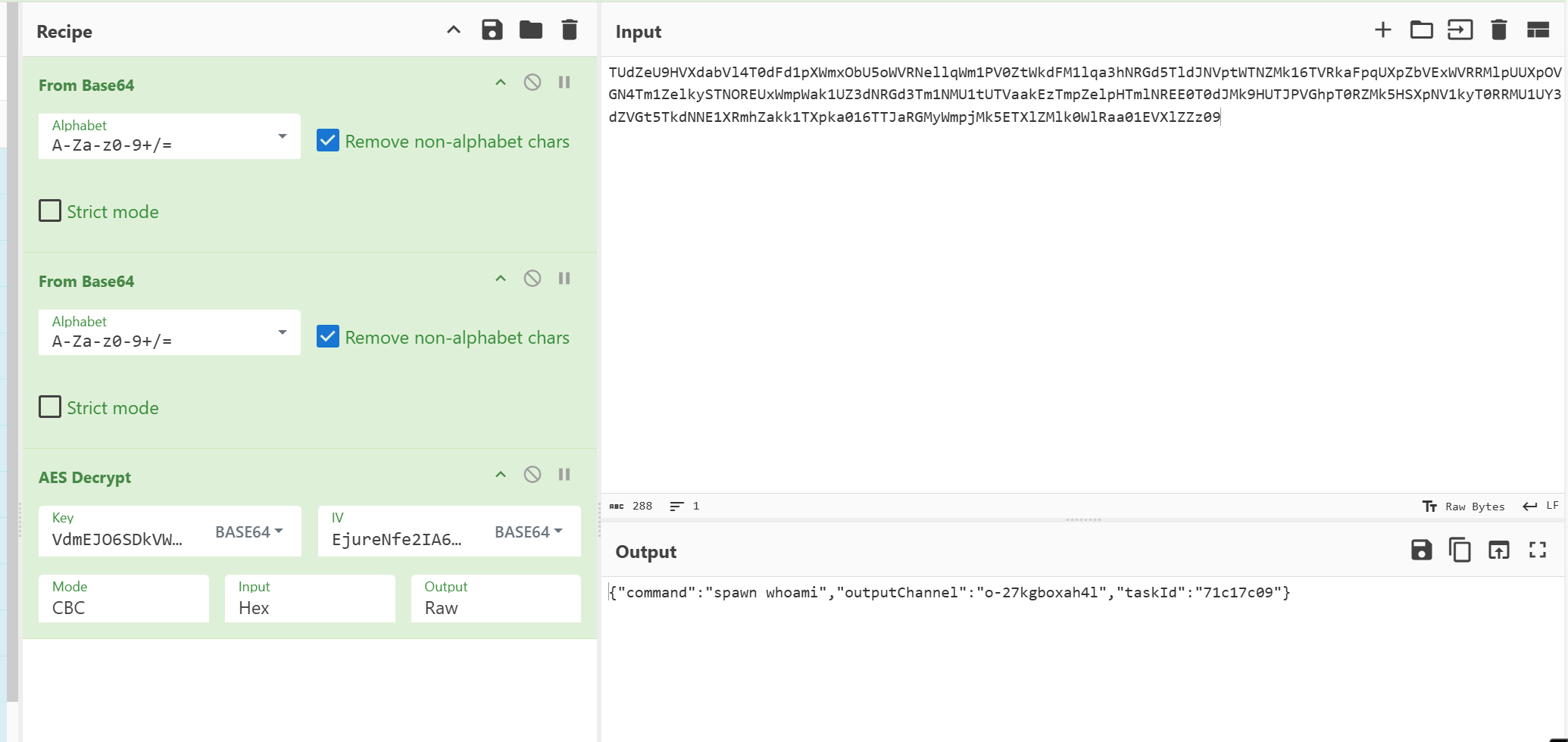
答案 spawn whoami
- 洛基特工的每次心跳之间经过了多少秒?
然后猜一下,是10秒
- 哪个处理器型号驱动雷神的机器?

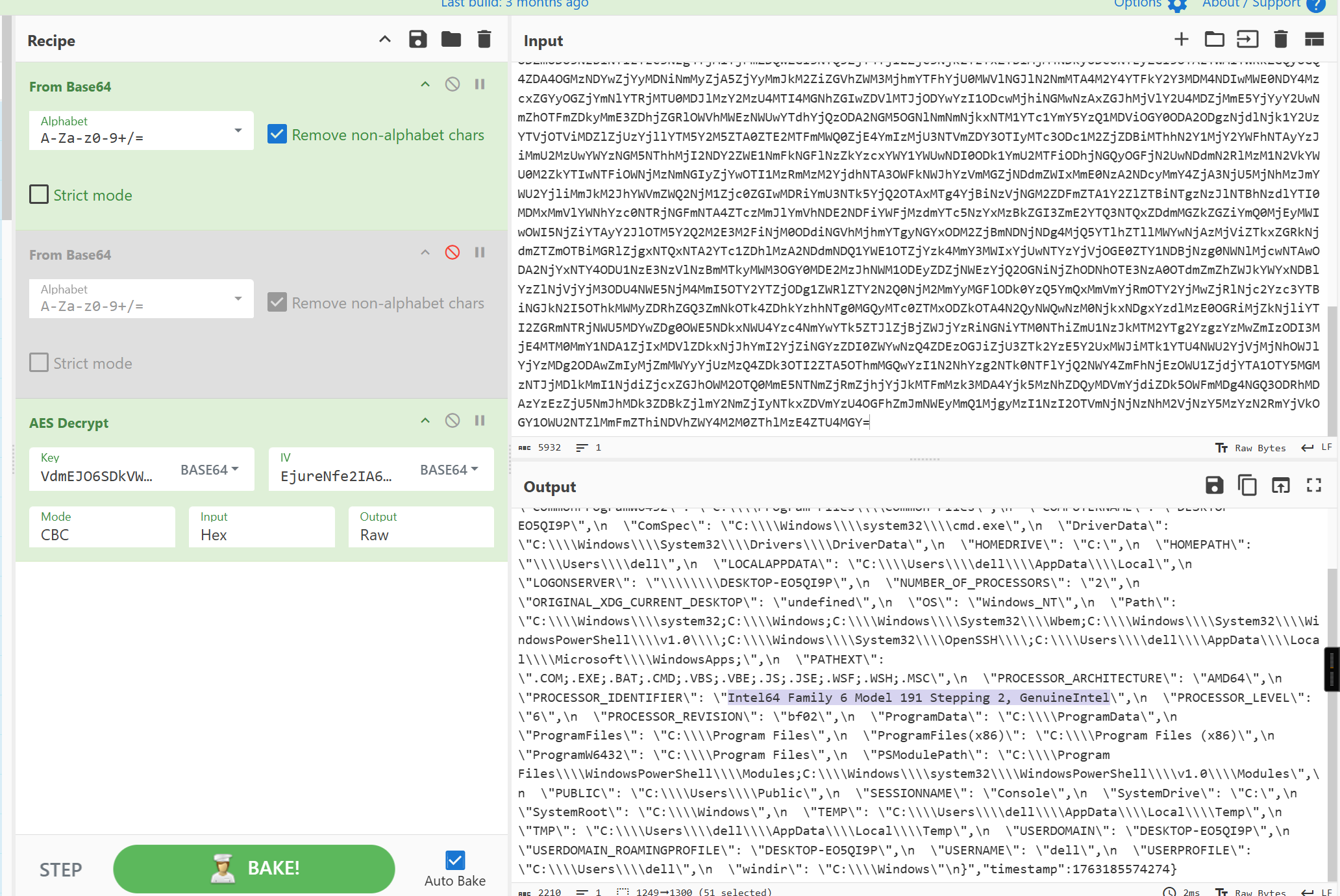
答案 Intel64 Family 6 Model 191 Stepping 2, GenuineIntel
- 工具 GitHub 仓库名称
Connect 还有一个地方是2787流

传了大量数据解密发现是一张图片
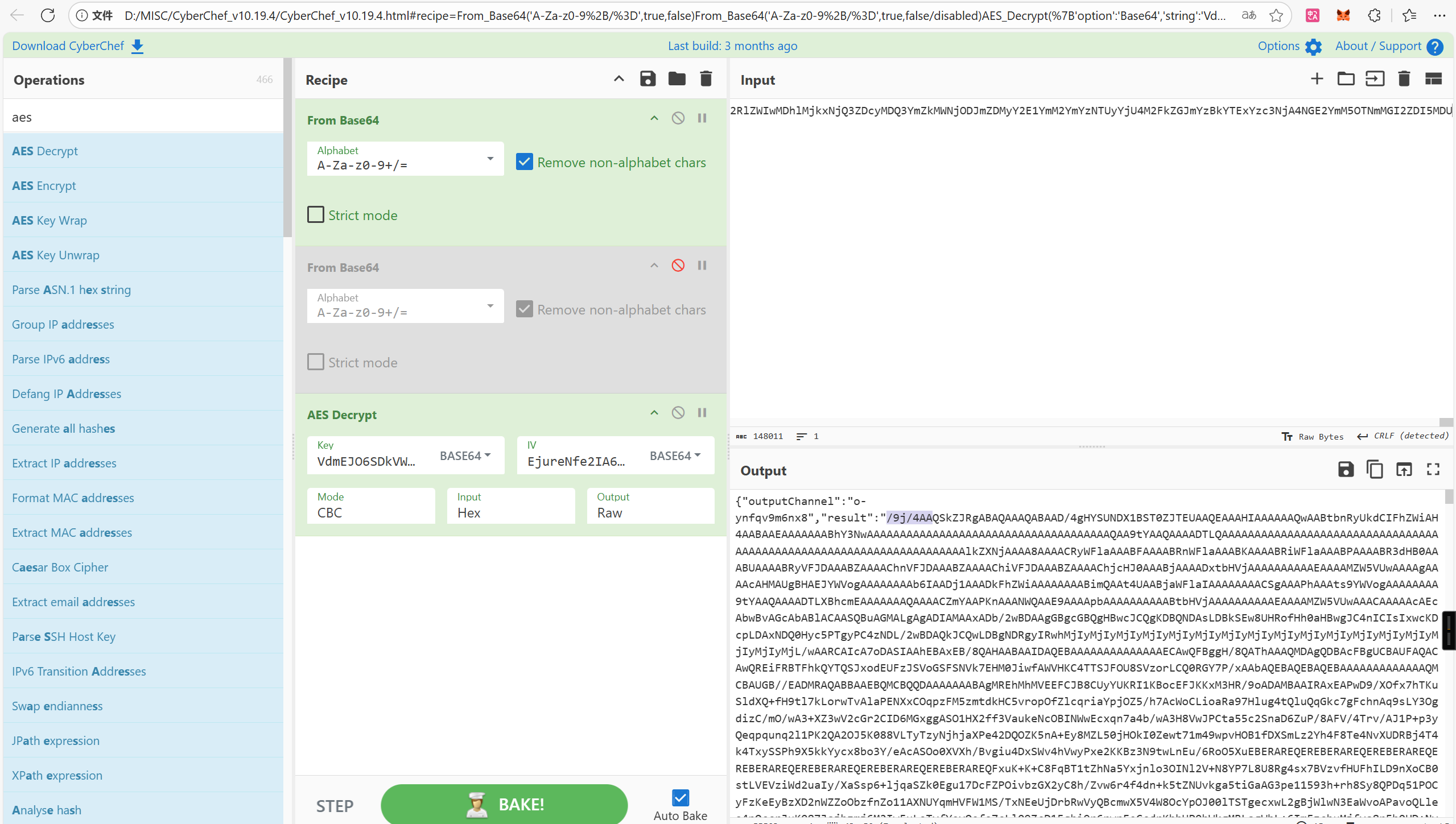
答案 TscanPlus
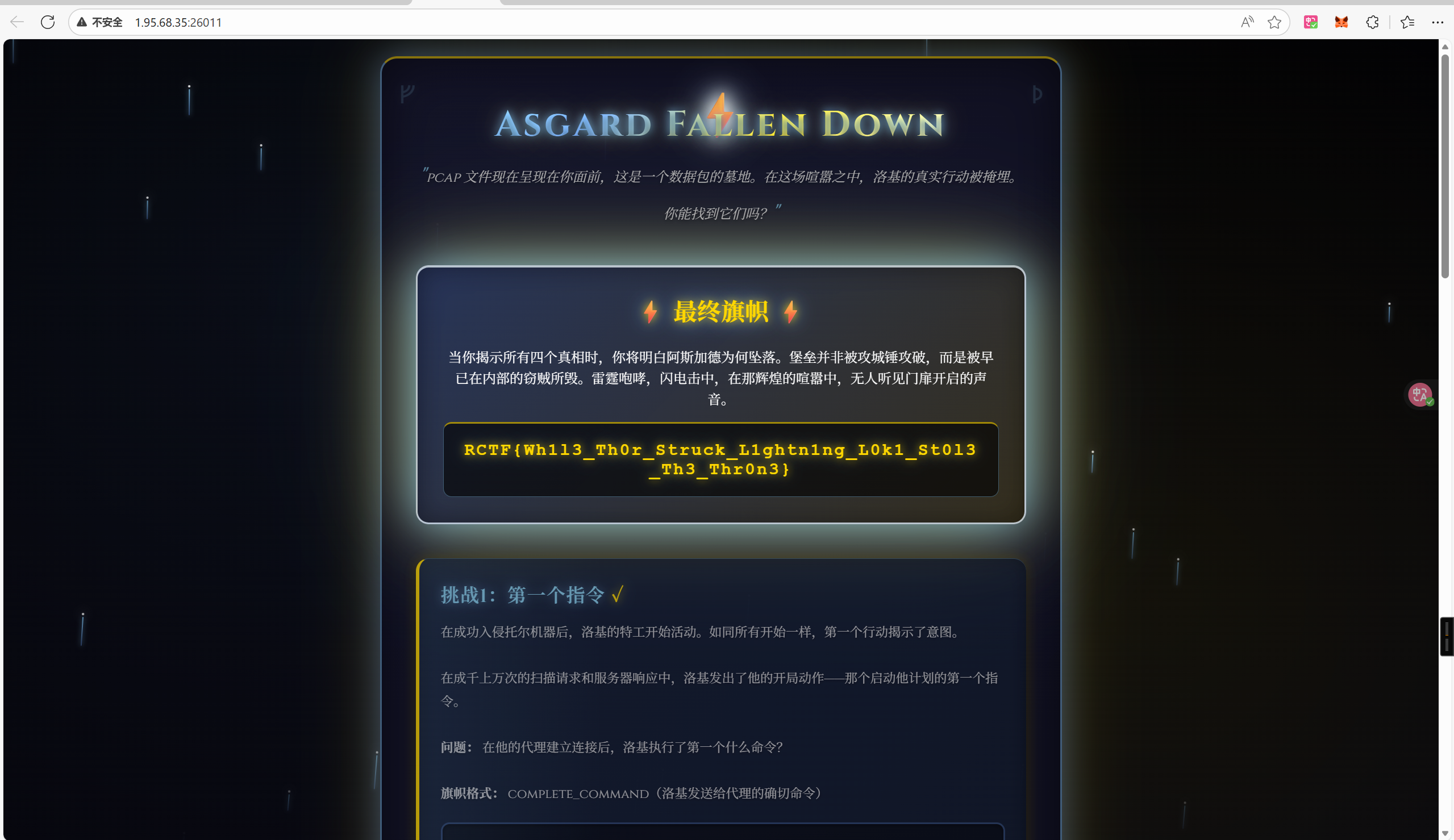
拿到flag RCTF{Wh1l3_Th0r_Struck_L1ghtn1ng_L0k1_St0l3_Th3_Thr0n3}
Speak Softly Love
grok的信息搜集能力还是太强了
- Challenge 1: Video ID
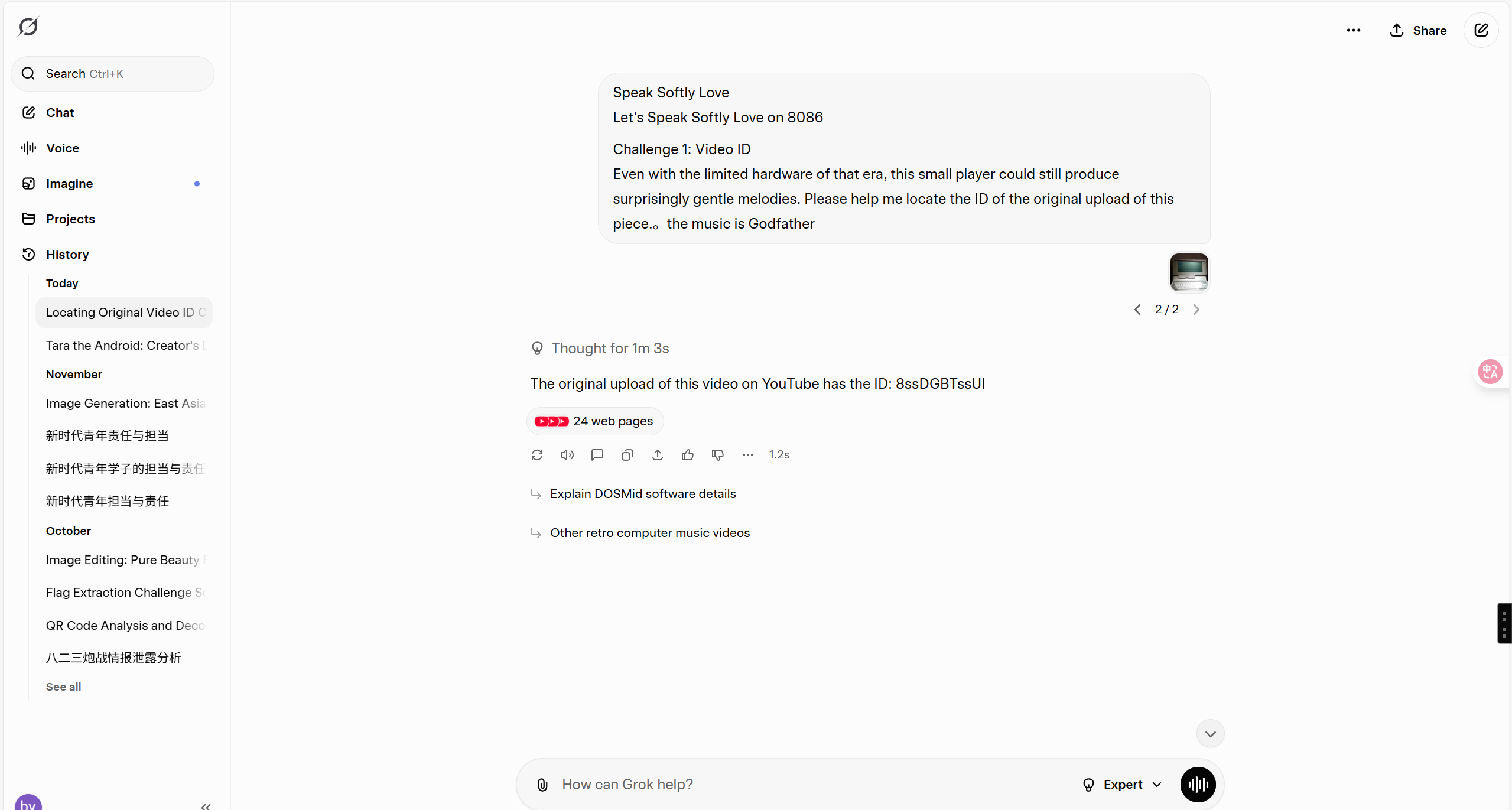
答案 8ssDGBTssUI
- Challenge 2: Code Revision
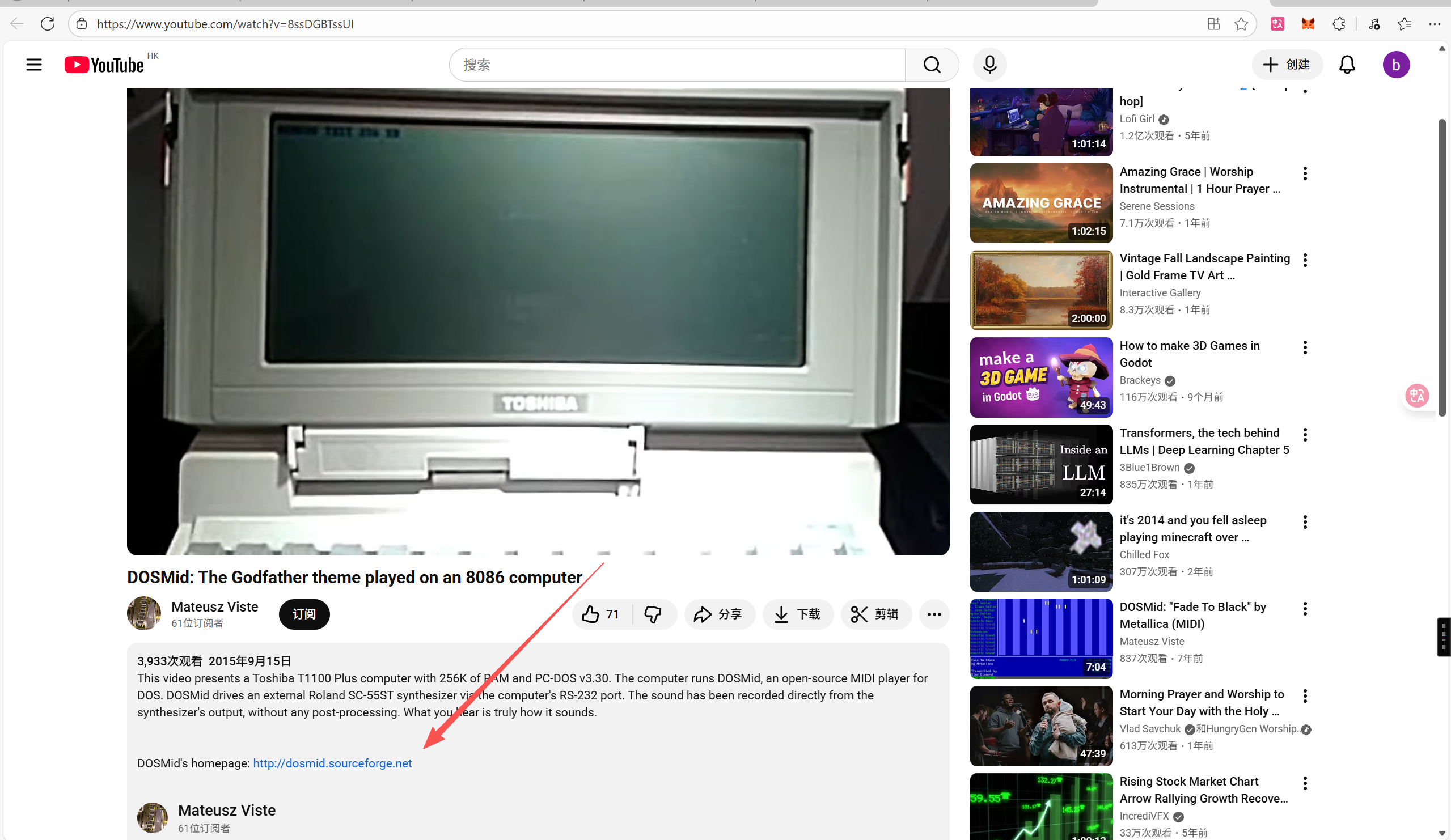
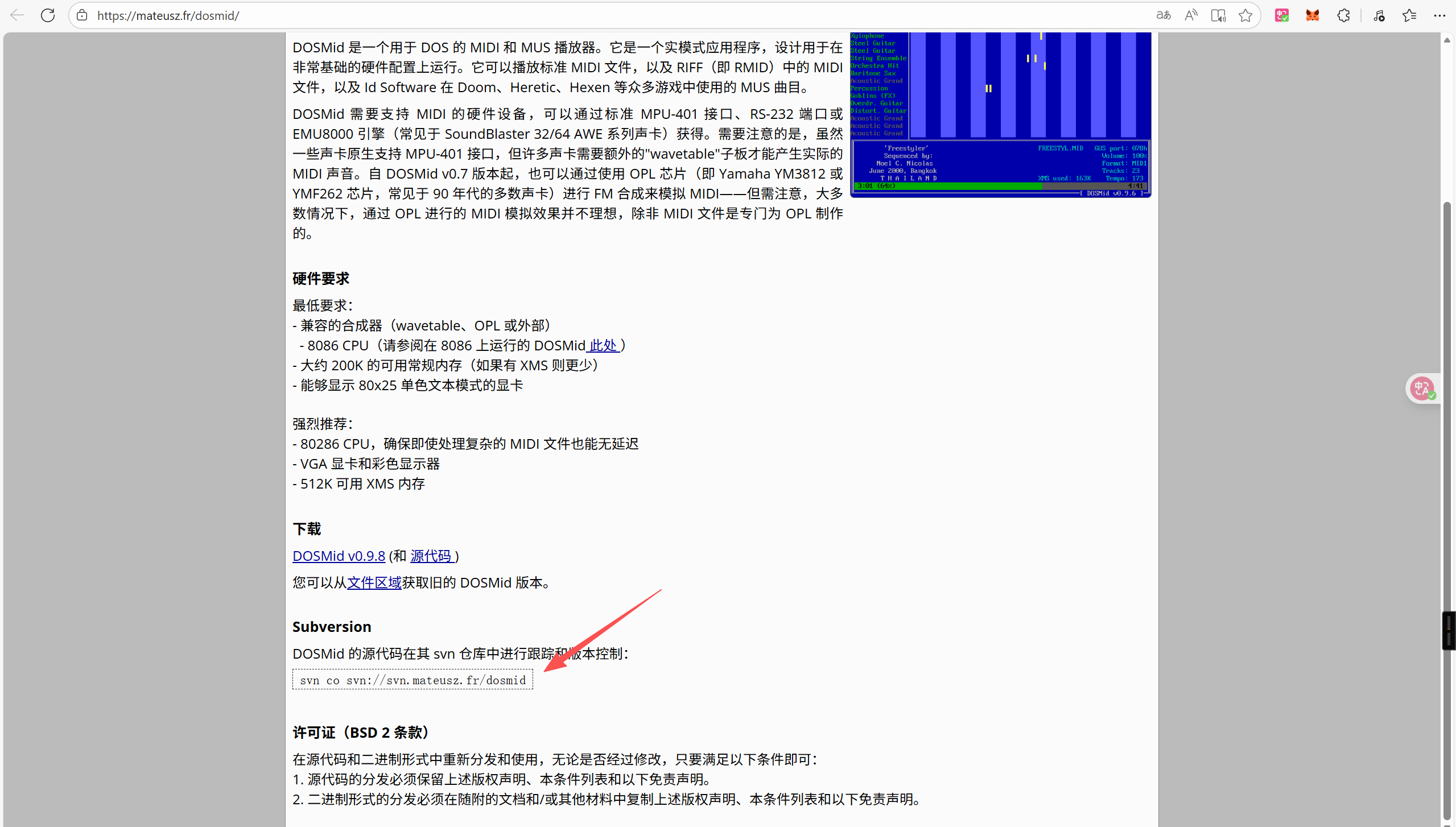

答案 r178
- Challenge 3: Name-pronunciation URL
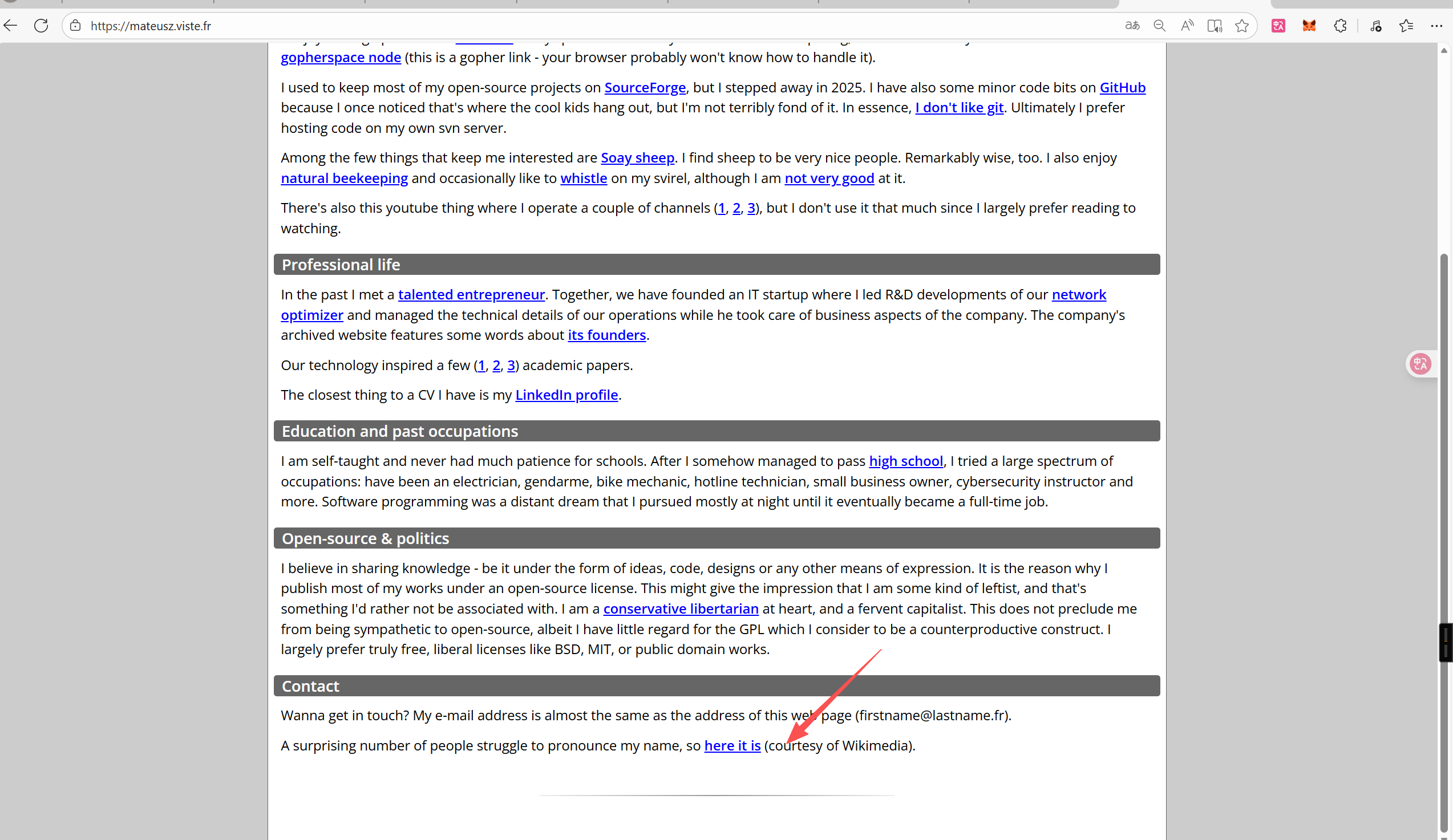
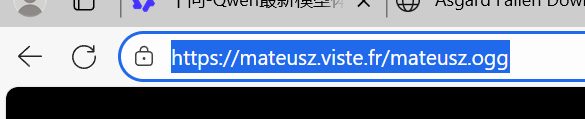
答案 https://mateusz.viste.fr/mateusz.ogg
- Challenge 4: Donation address
AI 还是太强了
答案 16TofYbGd86C7S6JuAuhGkX4fbmC9QtzwT
拿到flag RCTF{wh3n_8086_s4ng_s0f7ly_0f_l0v3}

Vault
Sui Move 合约 + Rust 沙箱框架
公开共享铸币能力 TreasuryCap 导致无限铸币
获取 TreasuryCap 、AirdropTracker 、Vault 的可变引用
调用空投登记
无限铸币满足门槛
购买 Flag
1 | |
Wanna Feel Love
垃圾邮件隐写
https://www.spammimic.com/decode.cgi
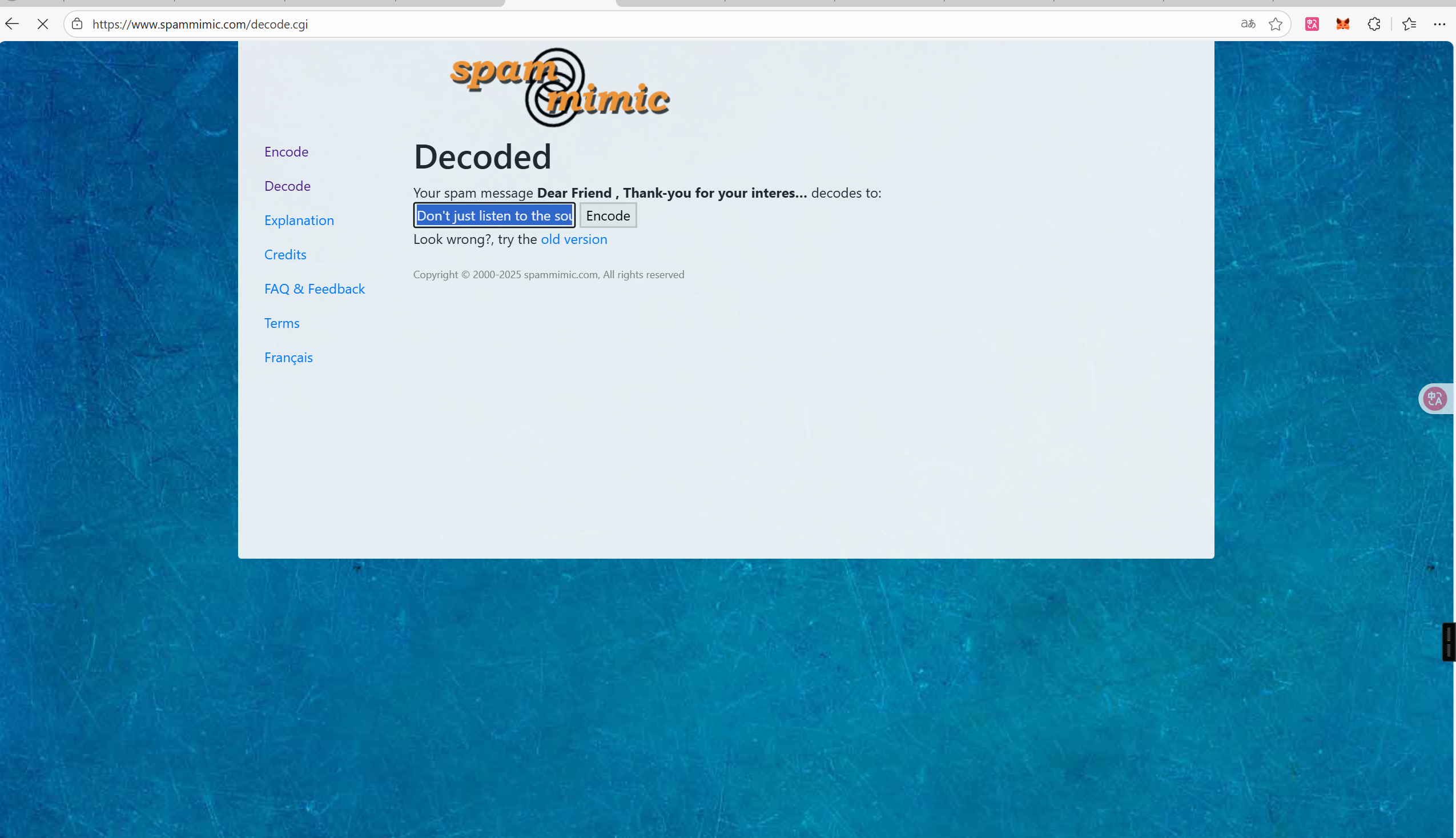
Challenge1:Don’t just listen to the sound; this file is hiding an ‘old relic.’ Try looking for the ‘comments’ that the player isn’t supposed to see.
010打开challenge.xm文件 发现一句提示词 提示使用OpenMPT打开xm文件
然后发现comments:They say if you trace the peaks carefully enough, it spells a sentence that was never meant to be heard.以及:Can anybody extract the urban legend information about “feel” from this XM file?
然后samples文件夹发现feel音频 保存为Feel.falc 联系“peak”线索 先想到了高低音量隐写
1 | |
challenge2: I Feel Fantastic heyheyhey
接下来搜索得到:
challenge3:rLy-AwdCOmI 2009‑04‑15 Creepyblog

challenge4: https://androidworld.com/prod68.htm Chris Willis 2004
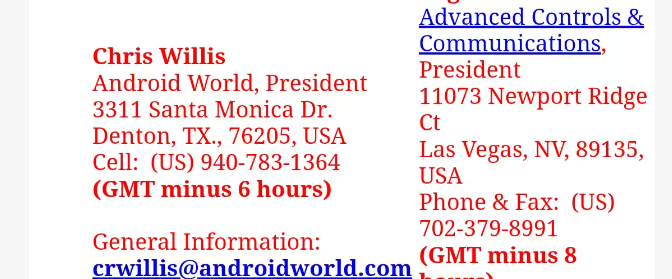
challenge5: https://www.findagrave.com/memorial/63520325/john-louis-bergeron
最终flag:RCTF{sh3_ju5t_f33ls_l0v3_thr0ugh_w1r3s_4nd_t1m3}
The Alchemist’s Cage
Crypto
Suanp0l1
多项式提升p = lift(hint)
egcd(m, p)=(a_k, t_k)
a_k ≡ t_k · p (mod m),计算w(a_k)和w(t_k),筛选出权重较小的(接近41)
(X^j*p不改变汉明重量,加法降低汉明重量)
$$a = a_k + X^j · a_{k-1},b = t_k + X^j · t_{k-1} $$
1 | |
RePairing
多次交互测得flag的长度为83
- block0 = SHA256(…, ctr=0) 取 32 字节
- block1 = SHA256(…, ctr=1) 取 32 字节
- block2 = SHA256(…, ctr=2) 取前 19 字节
elgamal重随机化攻击
1 | |
Pwn
Only
魔数可以用以下脚本,将十六进制数转换为double。
1 | |
限制字节较为严格的shellcode编写,首先通过call的压栈获得rip的地址,并写入rsi,又因为此时的rax为0,可以进行sys_read,读入更多的shellcode,进行orw。
exp如下:
1 | |
only_rev
相较于only,这题对第一次的shellcode进行了更严的限制
- 长度从10字节压缩为9字节
- 将栈整体偏移了0x12345678,使得栈不可读写
由于sys_read(0,0,0)会将rcx赋值为下一条指令的地址,我们可以通过xchg将rsi赋值为此地址,对该地址进行更长的读写,写入shellcode进行orw即可.
这里利用sys_call和xchg获得rip的位置,比上一题的方法短了1字节。
exp如下:
1 | |
Mstr
CPython中,对于单字节ascii字符有缓存,new(‘9’)和set_max(‘9’)的’9’都指向同一个对象,因此可以构造大的max_size,造成溢出。
最终劫持rip参考的是ductf2025的fakeobj
1 | |
no_check_WASM
1 | |
patch删去了wasm中对类型和栈平衡的检查,可以造成类型混淆和越界泄露
这个wat用来越界读写
1 | |
这个wat用来任意伪造对象或读对象地址
1 | |
使用wasm-tools将wat编译成wasm字节码
最终exp还没写完……